
IT Productivity Unlocks 71 Minutes Per Week
Lost productivity leads to lost revenue; unlocking productivity can come from surprising places

SD-WAN and Total Cost of Ownership
Considering the benefits of Secure SDWAN alongside Total Cost of Ownership (TCO)

Avoid These Top 5 IT Mistakes
Find out the most common mistakes, so you can get an "unfair advantage" in IT

A Fresh Perspective on Cyber Security Budgeting
Take a fresh, objective perspective to budgeting for Cyber; start with a true view of vulnerability

Top 5 Reasons For Vulnerability Scanning
5 of the most critical reasons to conduct a vulnerability scan right now

Outsourcing IT: Set Yourself Up For Success
Our guidance for structuring a successful relationship with an outsourced IT partner - we've seen it all!

Three Ways IT Leaders Can Get Ahead of the Annual Planning Process
Guidance for being proactive in annual planning. How to stay ahead and even as a demonstration of leadership.

New From L3 Networks: Technology Acceleration
Level up your IT roadmap with Technology Acceleration

Next Level Email Security Assessment: Insight Without Disruption
Email: Still the source of >90% of malware

Bridging the IT + Finance Divide
Benefit from our strong CFO partnerships to strengthen your own communication with finance and executive teams

DNS Security: Don't Settle for Anything Less than the Best
Your choice of DNS security matters -a lot. Value, performance and security risk need to be carefully weighed

Next Level Mobility Management
An evolving workforce - more mobile, less wired - requires a new level of Enterprise Mobility Management

Ransomware Impact Analysis
A next generation of tools are being used to identity and address ransomware risks in ways never before possible

The Increasing Risk in Cyber Insurance
Cyber insurance continues to increase in cost while narrowing its coverage areas; how to adopt a critical eye
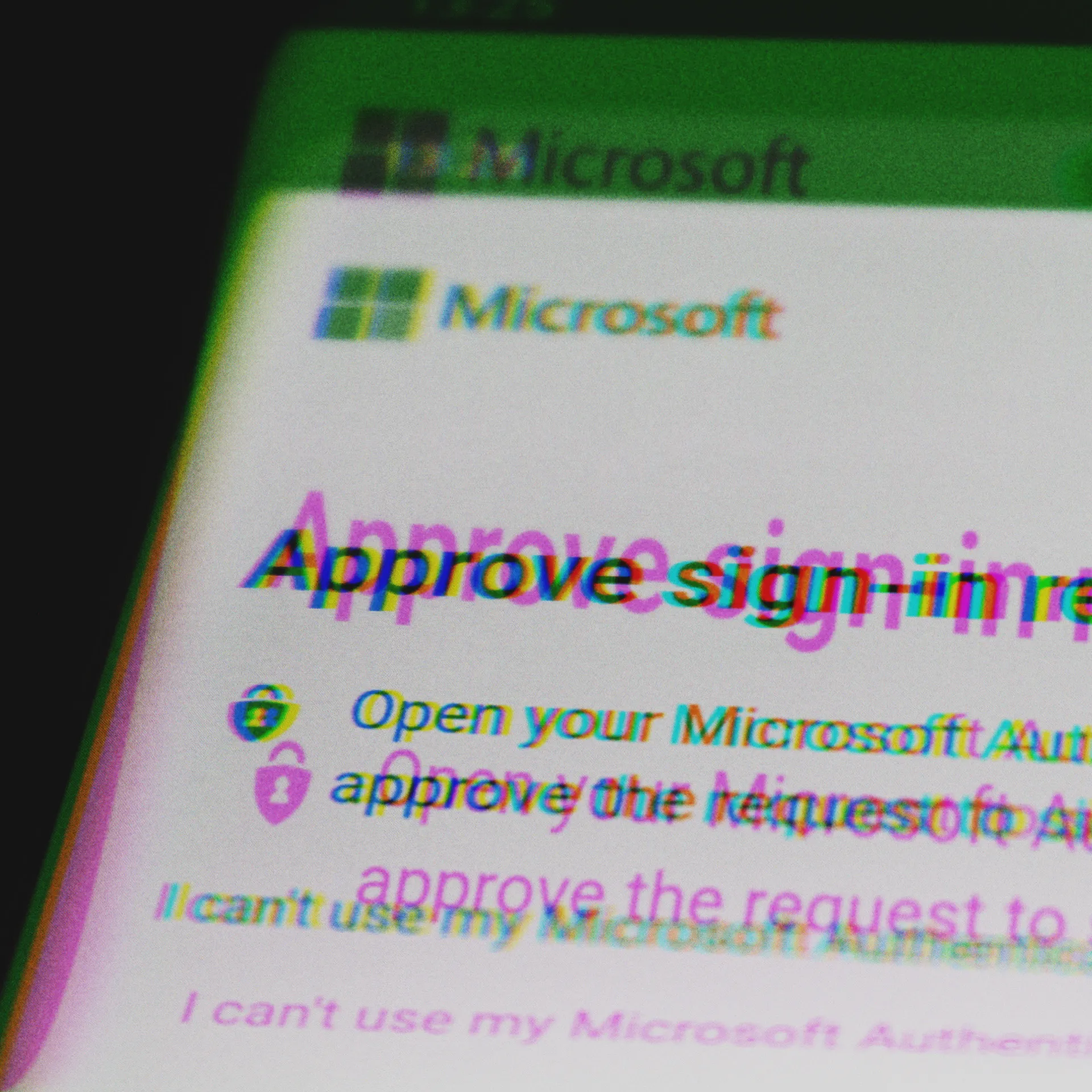
Benefits of Single Sign-On (SSO) for Enhanced Security and Efficiency
Single Sign-On (SSO) centralizes authentication, streamlines login processes, and enhances security with multi-factor authentication.

ThreatLocker Detect: Proactive Threat Detection and Response
Take a fresh, objective perspective to budgeting for Cyber; start with a true view of vulnerability

Application Control: Stop Threats Before They Start
Take a fresh, objective perspective to budgeting for Cyber; start with a true view of vulnerability

Elevation Control: Granting Privileges Without Compromising Security
Take a fresh, objective perspective to budgeting for Cyber; start with a true view of vulnerability

Network Control: Securing Every Connection
Take a fresh, objective perspective to budgeting for Cyber; start with a true view of vulnerability

Storage Control: Protecting Your Data at Every Point
Take a fresh, objective perspective to budgeting for Cyber; start with a true view of vulnerability

Configuration Manager: Simplifying Windows Configuration
Take a fresh, objective perspective to budgeting for Cyber; start with a true view of vulnerability

Why Professional Vulnerability Remediation Is Critical for Your Organizations Security
Take a fresh, objective perspective to budgeting for Cyber; start with a true view of vulnerability

Fortinet Zero Trust and L3 Networks: A Partnership for Comprehensive and Adaptive Cybersecurity
Take a fresh, objective perspective to budgeting for Cyber; start with a true view of vulnerability

Comprehensive Protection with L3 Networks and ThreatLocker: A Managed Approach
Take a fresh, objective perspective to budgeting for Cyber; start with a true view of vulnerability

Introduction to Zero Trust: A Comprehensive Approach for Securing Windows and Network Environments
Take a fresh, objective perspective to budgeting for Cyber; start with a true view of vulnerability
