Fortinet Zero Trust and L3 Networks: A Partnership for Comprehensive and Adaptive Cybersecurity
New to Zero Trust? Read our Intro to Zero Trust article to learn the basics.
Fortinet Zero Trust and L3 Networks: A Partnership for Comprehensive and Adaptive Cybersecurity
In an era where cybersecurity threats are more sophisticated than ever, the need for a comprehensive Zero Trust strategy has never been greater. Traditional perimeter-based security models are no longer sufficient in a world where users, devices, and applications operate across a diverse array of environments, both inside and outside of corporate networks. As organizations face increasingly complex threats, they require a security solution that not only protects against current risks but also evolves to counter new challenges. Fortinet’s Zero Trust Network Access (ZTNA) framework, powered by its Security Fabric, provides the robust, adaptive security needed to protect today’s dynamic digital landscapes. However, the true power of this technology is unlocked when it is paired with the expertise and continuous support of L3 Networks.
By choosing L3 Networks as your partner, you’re not just adopting a Zero Trust model—you’re ensuring that your network security evolves alongside the threats it faces. Together, Fortinet and L3 Networks provide a security solution that’s not only effective today but also adaptable to the challenges of tomorrow. This combination of cutting-edge technology and expert management delivers the kind of proactive, responsive security that modern organizations need to stay ahead in a constantly shifting threat landscape.
The Critical Importance of Zero Trust in Modern Cybersecurity
Zero Trust is a strategic approach to cybersecurity that assumes no entity—whether user, device, or application—should be trusted by default, even if it is within the network perimeter. Instead, Zero Trust demands continuous verification and validation of every interaction across the network. This model significantly reduces the attack surface and limits the potential damage that a breach could cause.
The urgency for a Zero Trust strategy has never been higher. With the rise of remote work, cloud adoption, and mobile devices, the traditional network perimeter has essentially dissolved. Cybercriminals are exploiting this expanded attack surface with increasingly sophisticated methods, such as advanced persistent threats (APTs), ransomware, and supply chain attacks. In this context, Zero Trust is not just an option—it’s a necessity.
- Key Point: Fortinet’s ZTNA framework, empowered by the Security Fabric, provides the advanced tools required to implement a true Zero Trust strategy. But the success of this strategy hinges on how well it is managed and optimized over time. This is where L3 Networks plays a pivotal role, ensuring that your Zero Trust framework remains effective, resilient, and adaptive.
How Fortinet’s Security Fabric Powers Zero Trust
At the core of Fortinet’s ZTNA solution is the Security Fabric, a comprehensive architecture that integrates all Fortinet products into a unified security system. The Security Fabric enables seamless communication between different security layers, allowing for real-time data sharing and coordinated threat responses across the network. This interconnected framework is what makes Fortinet’s Zero Trust approach so powerful, providing the flexibility and scalability needed to secure complex, distributed environments.
Unified Communication Across the Security Fabric:
Fortinet’s Security Fabric ensures that all security products—from firewalls to endpoint protection to cloud security—are interconnected. For example, if a client on the network running FortiClient detects a potential vulnerability or compliance issue, this information is immediately communicated across the Security Fabric. Other Fortinet products, such as FortiGate or FortiAuthenticator, can then adjust their policies in real-time, either restricting access or triggering additional security measures. This unified communication ensures that every component of the network operates under a consistent Zero Trust policy.
Dynamic Policy Enforcement:
The integration provided by the Security Fabric enables dynamic policy enforcement across the network. Security decisions are made based on real-time data from across the environment, allowing the network to adapt to changing conditions instantly. For instance, if a device fails a compliance check or is flagged for suspicious behavior, the Security Fabric can automatically quarantine the device, restrict its access, or trigger a vulnerability scan. This dynamic enforcement of policies ensures that threats are neutralized before they can escalate.
Comprehensive Orchestration:
The Security Fabric also enables orchestration across the entire ZTNA environment. This means that security policies are not just applied but are consistently enforced across all segments of the network. Features like automatic group assignment ensure that users are always placed in the appropriate security groups based on real-time data. This orchestration significantly reduces the risk of unauthorized access and ensures that the network remains secure even as conditions change.
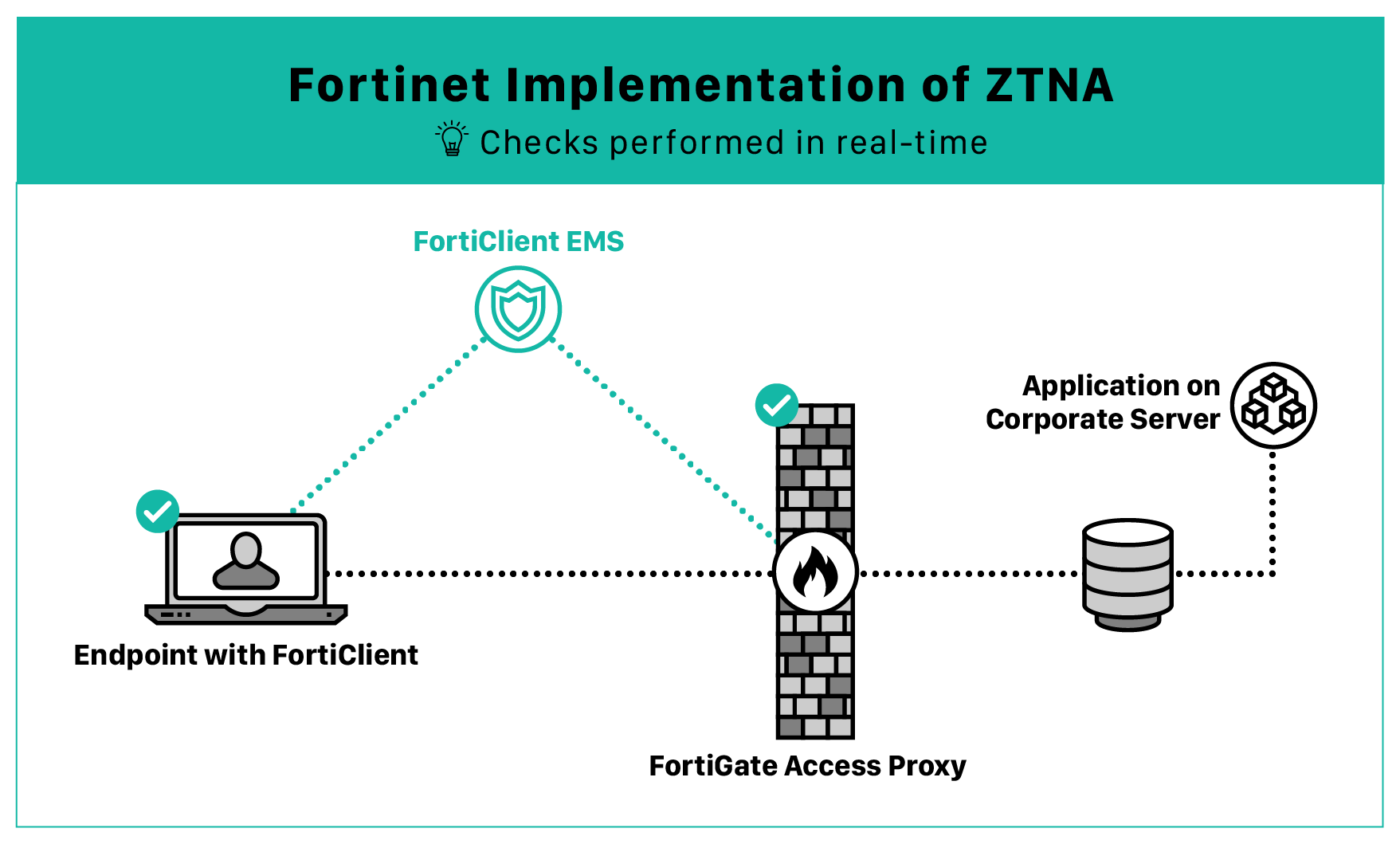
Advanced Technical Features of Fortinet ZTNA
Fortinet’s Zero Trust model goes beyond simple access control. It involves continuous assessment and verification of the trustworthiness of devices, users, and applications across the network. Here’s how Fortinet’s ZTNA framework delivers superior security:
Real-Time Endpoint Compliance and Quarantine:
A key feature of Fortinet’s ZTNA is its ability to assess endpoint compliance in real-time. Every device connecting to the network must meet stringent security criteria, such as up-to-date patches, correct configurations, and the absence of known vulnerabilities. Devices that fail these checks are automatically quarantined by the Security Fabric. This quarantine action is enforced across the network, ensuring that non-compliant or potentially compromised devices cannot access critical resources until they are remediated.
Automated Vulnerability Assessments:
Fortinet’s ZTNA framework includes automated vulnerability assessments that continuously scan endpoints for potential weaknesses. These assessments are not merely for reporting purposes; they feed directly into the Security Fabric, influencing real-time security decisions. For example, if a vulnerability is detected on an endpoint, that device’s access permissions can be immediately adjusted, restricting ingress or egress traffic until the issue is resolved. This proactive approach ensures that vulnerabilities are addressed before they can be exploited by attackers.
Patch Policy Enforcement:
Keeping endpoints updated with the latest security patches is a critical aspect of maintaining network security. Fortinet’s Security Fabric automates patch policy enforcement across all connected devices. If a device is found to be out of compliance—perhaps due to a missed critical update—it is flagged, and its network access is restricted until the patch is applied. This automated process ensures that all devices remain compliant with the organization’s security policies, thereby reducing the risk of a breach due to outdated software.
L3 Networks: The Essential Partner in Fortinet Zero Trust Deployment
While Fortinet’s ZTNA framework provides a powerful toolset for implementing Zero Trust, the effectiveness of this technology depends heavily on expert deployment, management, and continuous optimization. L3 Networks specializes in providing these services, ensuring that your Zero Trust strategy is not only robust but also adaptive to the ever-changing threat landscape.
Strategic Deployment and Integration:
L3 Networks begins by conducting a thorough assessment of your existing network infrastructure. This assessment identifies areas where Fortinet’s ZTNA solutions can be most effectively deployed to maximize security and efficiency. Our team then handles the entire deployment process, from initial configuration to full integration with your existing systems. This strategic approach ensures that the Security Fabric operates seamlessly across your network, enabling real-time communication and dynamic policy enforcement.
24/7 Monitoring and Threat Response:
The success of a Zero Trust strategy hinges on continuous monitoring and the ability to respond to threats in real-time. L3 Networks provides this through our dedicated Security Operations Center (SOC), which operates around the clock. Our SOC analysts monitor your network for signs of compromise, suspicious activity, or policy violations, allowing us to respond immediately to any potential threats. This proactive monitoring ensures that your Zero Trust framework remains effective and that any emerging threats are neutralized before they can cause significant harm.
Continuous Policy Management and Optimization:
Zero Trust is not a “set it and forget it” solution—it requires ongoing management to remain effective. L3 Networks takes on the responsibility of continuously refining and optimizing your Zero Trust policies. This includes regular reviews of access controls, updates to compliance requirements, and adjustments based on emerging threats. By continuously managing these aspects, L3 Networks ensures that your Zero Trust environment remains resilient and aligned with your organization’s evolving needs.
Why L3 Networks and Fortinet ZTNA Are a Winning Combination
The combination of Fortinet’s advanced technology and L3 Networks’ expert management creates a security solution that is both comprehensive and adaptive. By leveraging the power of the Security Fabric, L3 Networks ensures that your organization’s Zero Trust framework remains dynamic, adjusting to new threats and challenges as they arise.
Benefits of Partnering with L3 Networks:
- Proactive Threat Defense: With continuous monitoring and real-time response, L3 Networks ensures that threats are detected and mitigated before they can cause significant damage.
- Simplified Compliance: Fortinet’s Security Fabric inherently supports regulatory compliance, and L3 Networks enhances this by managing the compliance process, reducing the risk of violations.
- Operational Efficiency: L3 Networks’ managed services allow your internal IT team to focus on strategic initiatives, knowing that your network’s security is in expert hands.
- Scalability and Flexibility: As your organization grows, L3 Networks ensures that your Zero Trust framework scales with your needs, adapting to new environments, technologies, and regulations.
Moving Forward: Embracing Adaptive Security with Fortinet and L3 Networks
In today’s fast-paced digital world, the cybersecurity landscape is constantly evolving, with new threats emerging at an unprecedented rate. The need for a comprehensive, adaptive security strategy has never been more critical. Fortinet’s Zero Trust Network Access framework, powered by the Security Fabric, provides the foundation for such a strategy. However, to fully realize the potential of this technology, organizations need a partner who can manage and optimize it over time.
By partnering with L3 Networks, you’re not just implementing a Zero Trust framework—you’re investing in a long-term security strategy that evolves with your business and the threats it faces. Together, Fortinet and L3 Networks offer a robust, adaptive security solution that protects your organization today and prepares it for the challenges of tomorrow.
Don’t leave your network security to chance. Choose L3 Networks as your trusted partner and take the first step towards building a resilient, future-proof cybersecurity strategy with Fortinet Zero Trust.
L3 Networks and Fortinet are proud to partner in delivering comprehensive and adaptive cybersecurity solutions. For additional resources on securing your business, explore DesignRush, a leading platform connecting businesses with top cybersecurity companies in the US.



